With the new information we acquired about the system call, the next task is to find out where the size of the hard disk is, and how we can change it. This piece of code creates a breakpoint for NtDeviceIoControlFile via our pafish-tycho-process, activates it and waits for the breakpoint. For this we have to change the total clusters and the free clusters. Preparation What exactly are system calls and why are they important for software analysis? And at the end, the Tycho Setup passes two more tests and a nice example script for Tycho is still finished. Especially not if you do this for the first time. What system calls are available depend on your operating system. 
| Uploader: | Digul |
| Date Added: | 21 January 2018 |
| File Size: | 20.15 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 29502 |
| Price: | Free* [*Free Regsitration Required] |
Automated Malware Analysis Report for - Generated by Joe Sandbox
This piece of code creates a breakpoint for NtDeviceIoControlFile via our pafish-tycho-process, activates it and waits for the breakpoint. All we need to do is to pause Pafish when this system call occurs. Motivation In order to gain first experiences in software analysis with Tycho, I was looking for a simple project that would still be useful.
There are four tests that trace the Tycho VM: Preparation What exactly are system calls and why are they important pafush software analysis? Hi, my name is Sebastian Manns. This task is very manageable, and it is easy to get familiar with different functions of Tycho.
[New Tool] Pafish v0.57 Malware Analysis Tool Released
We need to know how many clusters we need for these values. In this snippet of code we create a factory object which retrieves the input and output parameters of pafush system call.
System Calls are used to call a kernel service from user land. A pointer to a buffer that is to receive the device-dependent return information from the target device. The second test is similar to the first. This object contains the pfish that is interesting for us.
| - Free Malware Sandbox Online
Pafis gives us full control over the communication from a program to the operating system. So now we begin to find the system call. Trace number 1 comes from pafish taking the difference between two CPU timestamp counter values.

As an example we want to manipulate the system call so that the partition is GiB and still has GiB free space. First we import the most important libraries, which are needed for the breakpoints and the evaluation of the system calls. For this we use the following calculation:. Especially not if you do this for the first time. In my first blog entry I will show you how easy it is to evaluate and manipulate system calls with Tycho using Pafish as an example.
After that, we wait until pafish. The interpretation works also similarly to the first test.
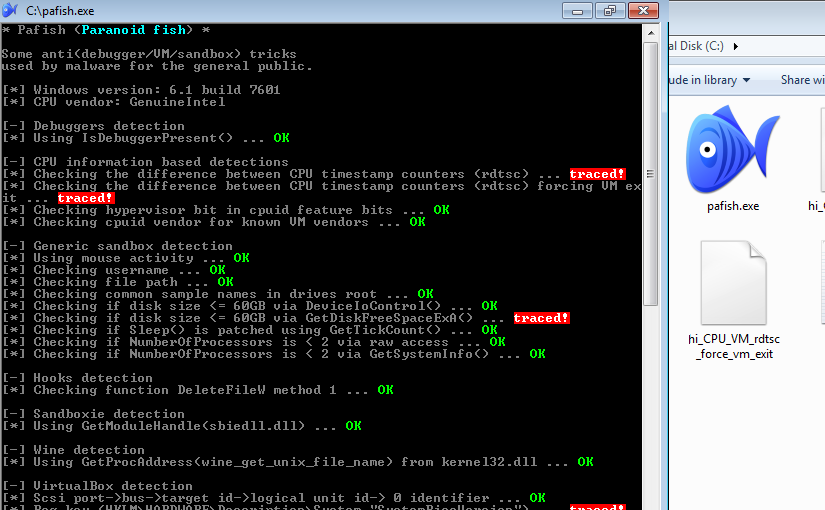
Furthermore Tycho exposes much less virtualization artifacts than other off-the-shelf virtualization software, which is a big advantage in malware analysis. With the new information we acquired about the system call, the next task is to find out where the size of the hard disk is, and how we can change it.
Because you can easily get complete information from a system call before and after execution, you can quickly find out a lot about the software. How to reach us Cyberus Technology GmbH service cyberus-technology.
We can stop the program at any system call, evaluate and manipulate it and let the program run again. We add NtQueryVolumeInformationFile to the whitelist and the system call interpretation retrieves the following information after the breakpoint was hit:. Currently Tycho is not completely invisible for Pafish: How to pause a program with breakpoints on a system call is also described in the previous article Windows system call parameter analysis.
Now that we have the right system call and know what it does, it is super easy to manipulate it with Tycho. In this blog entry I showed you how easy it is to pxfish, stop, analyze and manipulate system calls with tycho.
Then we connect to the Tycho server and with service. Some of them are essentials while other help us improve your experience. And all this without even psfish at a traditional debugger and dealing with assembler code. Trace number 2 comes from the fact that the mouse remains untouched on the analysis system.


Комментарии
Отправить комментарий